Britain's domestic intelligence agency has issued an urgent security warning to parliamentarians about ongoing Chinese espionage attempts targeting Westminster through professional networking platforms.
The LinkedIn Approach: A Modern Spy Technique
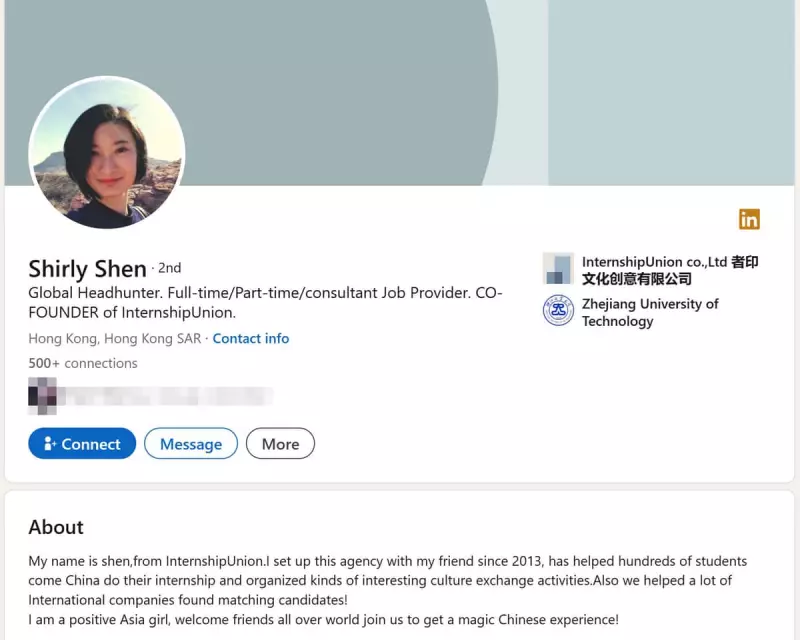
According to security sources, Chinese operatives are using recruitment consultants like Shirly Shen and Amanda Qiu to approach MPs, peers, their staff, economists, and thinktank researchers. The approach typically begins with an unexpected LinkedIn connection request from what appears to be a young female headhunter based in China.
The recruitment pitch offers lucrative part-time work opportunities, typically around £20,000 for writing geopolitical reports that require "non-public" or "insider" insights. Preferred payment methods include cryptocurrency or cash, avoiding traditional banking channels that might raise suspicions.
Scale of the Threat and Official Response
This isn't the first time MI5 has raised alarms about Chinese online recruitment activities. In 2023, MI5 chief Ken McCallum revealed Chinese agents had approached approximately 10,000 Britons on LinkedIn over the preceding two and a half years, seeking political, industrial, military and technological secrets.
The latest campaign specifically targeting politicians and parliamentary figures prompted the spy agency to distribute a security alert through the offices of Commons Speaker Lindsay Hoyle and his Lords counterpart. Although MI5 didn't publicly release the security briefing, the agency anticipated it would leak once emailed to parliament, ensuring wider public awareness.
Security Minister Dan Jarvis described China's activities as a "covert and calculated" effort to recruit British political figures, telling MPs that Beijing maintains "a low threshold for what information is considered to be of value."
Legal Changes and Geopolitical Context
The security alert comes following the embarrassing collapse of prosecution against former parliamentary aide Christopher Cash and his friend Christopher Berry, who had been accused of spying for China. The case failed on a technicality under the now-repealed Official Secrets Act, highlighting gaps in Britain's legal protections against espionage.
The MI5 briefing specifically references the new National Security Act, warning that "those engaging in espionage activity risk significant criminal penalties." The legislation makes it illegal to engage in conduct that "materially assists a foreign intelligence service."
Experts note that China's intelligence apparatus is vast, employing an estimated 300,000 people. Chris Inglis, a US national cyber director under President Joe Biden, observed that "the Chinese have more English speakers engaged in this than we [western intelligence] have English speakers."
Beijing's strategy involves cultivating sources over the long term, recognizing that individuals who might seem peripheral today could become significant with sudden political changes. The approach reflects China's broader geopolitical contest with western nations, operating below the threshold of outright war but including sophisticated hacking campaigns like Salt Typhoon and Volt Typhoon that have compromised systems in dozens of countries.
Security officials emphasize that while LinkedIn interactions may seem less toxic than those on platforms like X or Facebook, they still carry significant risks when approached by sophisticated state actors pursuing long-term intelligence gathering objectives.





